JINIers
Google Cloud HA VPN 구성하기 본문
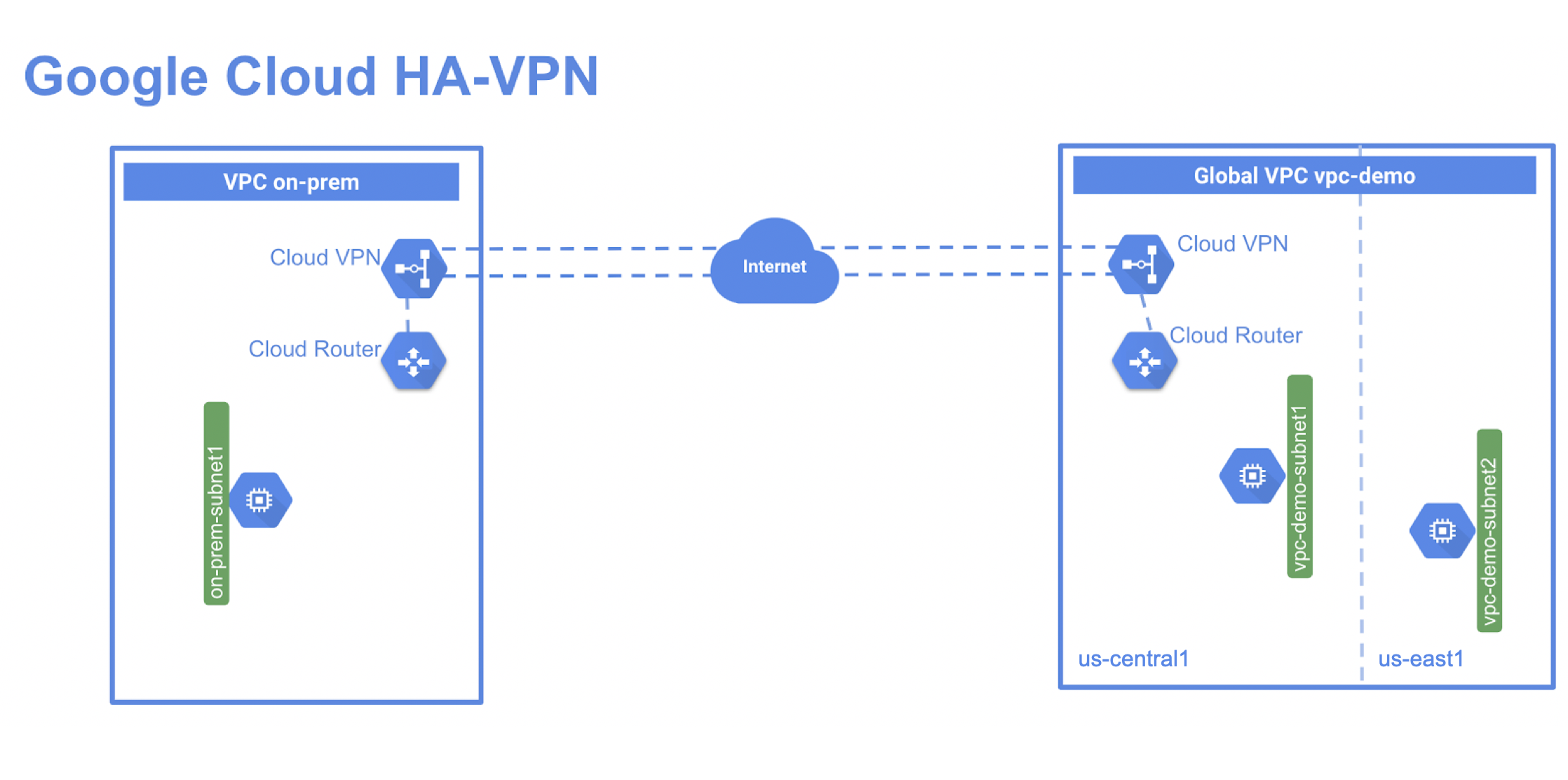
개요
- vpc 2개 생성
- 방화벽 규칙 생성
- vpn gw 생성
- bgp 피어링 생성
- vpn 터널 확인
목표
- 2개의 vpc 네트워크와 인스턴스 생성
- HA VPN 게이트웨이 구성
- VPN 터널로 동적 라우팅 구성
- 전역 동적 라우팅 모드 구성
- HA VPN gw 구성 확인 및 테스트
생각보다 어렵다. 잘 따라해보자.
작업1. 전역 vpc 환경설정
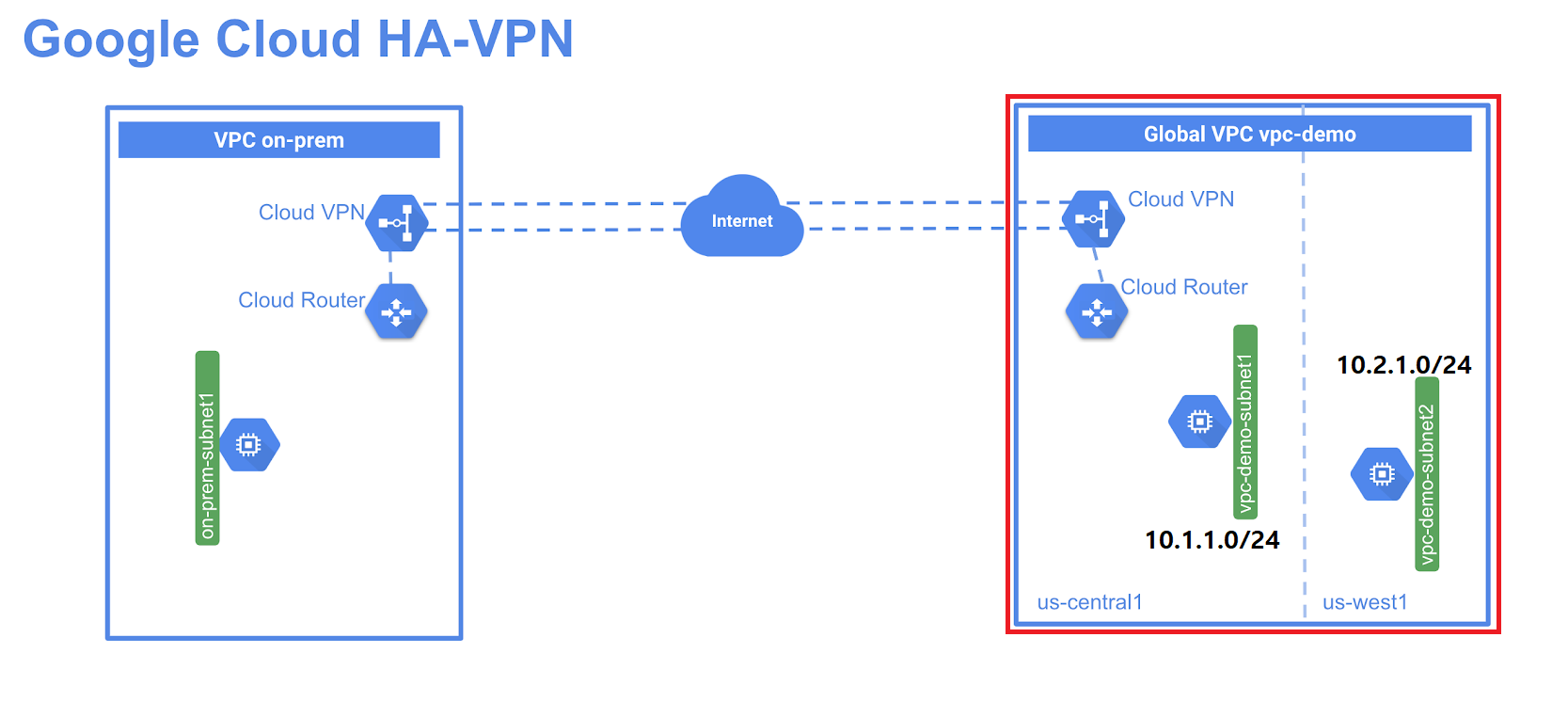
[vpc 설정]
# demo vpc 생성
gcloud compute networks create [vpc명] --subnet-mode custom
gcloud compute networks create vpc-demo --subnet-mode custom
# demo vpc subnet 생성(us-central1)
gcloud compute networks subnets create [vpc-subnet명] --network [vpc명] --range [ip/24] --region [지역명]
gcloud compute networks subnets create vpc-demo-subnet1 \
--network vpc-demo --range 10.1.1.0/24 --region us-central1
# demo vpc subnet 생성(us-east1)
gcloud compute networks subnets create [vpc-subnet명] --network [vpc명] --range [ip/24] --region [지역명]
gcloud compute networks subnets create vpc-demo-subnet2 \
--network vpc-demo --range 10.2.1.0/24 --region us-east1
[방화벽 규칙 설정]
# demo-vpc 내 모든 트래픽 allow
gcloud compute firewall-rules create vpc-demo-allow-custom \
--network vpc-demo \
--allow tcp:0-65535,udp:0-65535,icmp \
--source-ranges 10.0.0.0/8
# ssh, icmp 트래픽 허용 방화벽 규칙 생성
gcloud compute firewall-rules create vpc-demo-allow-ssh-icmp \
--network vpc-demo \
--allow tcp:22,icmp
[인스턴스 생성]
# region=us-central1-b
gcloud compute instances create vpc-demo-instance1 --zone us-central1-b --subnet vpc-demo-subnet1
# region=us-east1-b
gcloud compute instances create vpc-demo-instance2 --zone us-east1-b --subnet vpc-demo-subnet2
작업2. 시뮬레이션된 온프레미스 환경설정하기
[on-prem vpc 생성]

# vpc 생성
gcloud compute networks create on-prem --subnet-mode custom
# subnet 생성
gcloud compute networks subnets create on-prem-subnet1 \
--network on-prem --range 192.168.1.0/24 --region us-central1
[방화벽 규칙 설정]
# on-prem vpc 내 모든 트래픽 allow
gcloud compute firewall-rules create on-prem-allow-custom \
--network on-prem \
--allow tcp:0-65535,udp:0-65535,icmp \
--source-ranges 192.168.0.0/16
# ssh, rdp, http, icmp 트래픽 허용 방화벽 규칙 생성
gcloud compute firewall-rules create on-prem-allow-ssh-icmp \
--network on-prem \
--allow tcp:22,icmp
[인스턴스 생성]
gcloud compute instances create on-prem-instance1 --zone us-central1-a --subnet on-prem-subnet1작업3. HA VPN 게이트웨이 설정
순서
(1) 게이트웨이 생성
(2) 라우터 생성
[gateway 생성]
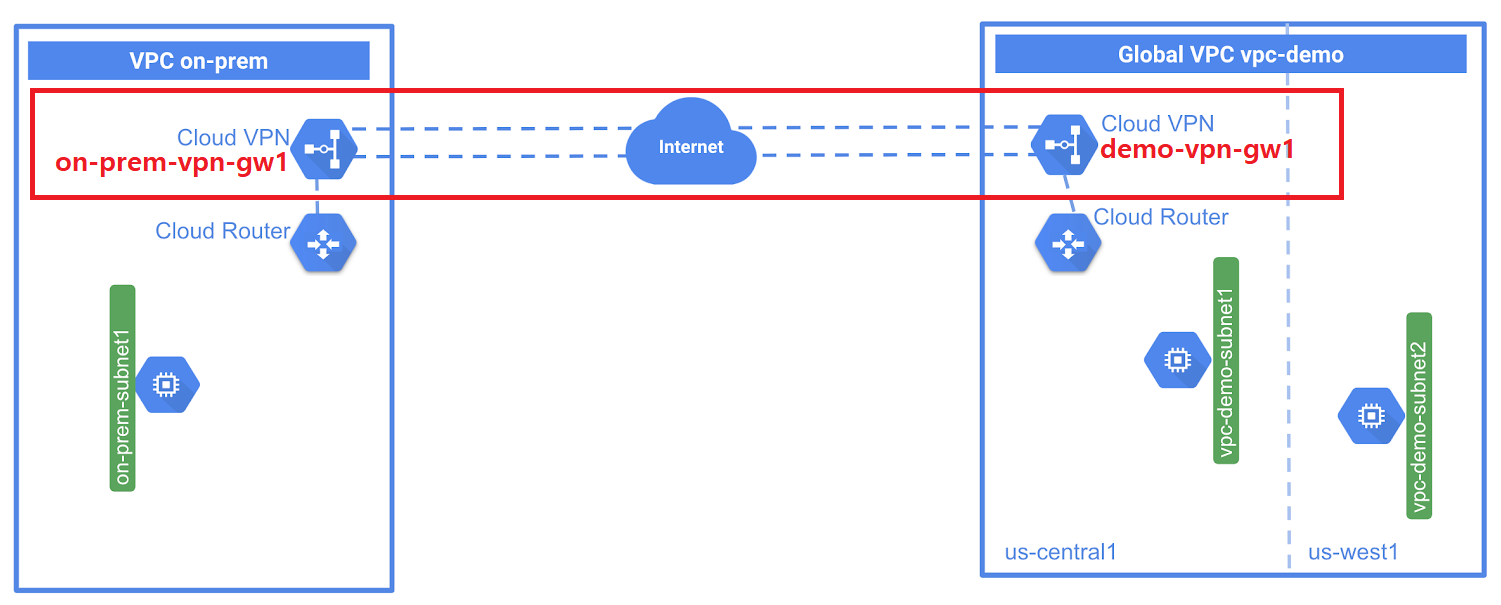
# demo-vpc gw 생성
gcloud compute vpn-gateways create [vpc-게이트웨이명] --network [vpc명] --region [지역명]
gcloud compute vpn-gateways create vpc-demo-vpn-gw1 --network vpc-demo --region us-central1
# on-prem gw 생성
gcloud compute vpn-gateways create [vpc-게이트웨이명] --network [vpc명] --region [지역명]
gcloud compute vpn-gateways create on-prem-vpn-gw1 --network on-prem --region us-central1
# gw 세부정보 조회
gcloud compute vpn-gateways describe vpc-demo-vpn-gw1 --region us-central1
gcloud compute vpn-gateways describe on-prem-vpn-gw1 --region us-central1
[라우터 생성]

# demo-vpc router
gcloud compute routers create [gw와 연결할 라우터명] --region [지역명] --network [vpc명] --asn [asn번호]
gcloud compute routers create vpc-demo-router1 \
--region us-central1 \
--network vpc-demo \
--asn 65001
# on-prem router
gcloud compute routers create [gw와 연결할 라우터명] --region [지역명] --network [vpc명] --asn [asn번호]
gcloud compute routers create on-prem-router1 \
--region us-central1 \
--network on-prem \
--asn 65002작업4. VPN 터널 2개 만들기

[vpc-demo vpn tunnel]
# interface 0
gcloud compute vpn-tunnels create [vpn-터널명] \
--peer-gcp-gateway [피어링할 반대편 게이트웨이명] \
--region [지역명] \
--ike-version 2 \
--shared-secret [SHARED_SECRET] \
--router [해당 라우터명] \
--vpn-gateway [해당 게이트웨이명] \
--interface 0
gcloud compute vpn-tunnels create vpc-demo-tunnel0 \
--peer-gcp-gateway on-prem-vpn-gw1 \
--region us-central1 \
--ike-version 2 \
--shared-secret [SHARED_SECRET] \
--router vpc-demo-router1 \
--vpn-gateway vpc-demo-vpn-gw1 \
--interface 0
# interface 1
gcloud compute vpn-tunnels create [vpn-터널명] \
--peer-gcp-gateway [피어링할 반대편 게이트웨이명] \
--region [지역명] \
--ike-version 2 \
--shared-secret [SHARED_SECRET] \
--router [해당 라우터명] \
--vpn-gateway [해당 게이트웨이명] \
--interface 1
gcloud compute vpn-tunnels create vpc-demo-tunnel1 \
--peer-gcp-gateway on-prem-vpn-gw1 \
--region us-central1 \
--ike-version 2 \
--shared-secret [SHARED_SECRET] \
--router vpc-demo-router1 \
--vpn-gateway vpc-demo-vpn-gw1 \
--interface 1
[on-prem vpn tunnel]
# interface 0
gcloud compute vpn-tunnels create on-prem-tunnel0 \
--peer-gcp-gateway vpc-demo-vpn-gw1 \
--region us-central1 \
--ike-version 2 \
--shared-secret [SHARED_SECRET] \
--router on-prem-router1 \
--vpn-gateway on-prem-vpn-gw1 \
--interface 0
# interface 1
gcloud compute vpn-tunnels create on-prem-tunnel1 \
--peer-gcp-gateway vpc-demo-vpn-gw1 \
--region us-central1 \
--ike-version 2 \
--shared-secret [SHARED_SECRET] \
--router on-prem-router1 \
--vpn-gateway on-prem-vpn-gw1 \
--interface 1작업5. 각 터널에 대한 경계 게이트웨이 프로토콜(BGP) 피어링 만들기
[vpc-demo tunnel 만들기]
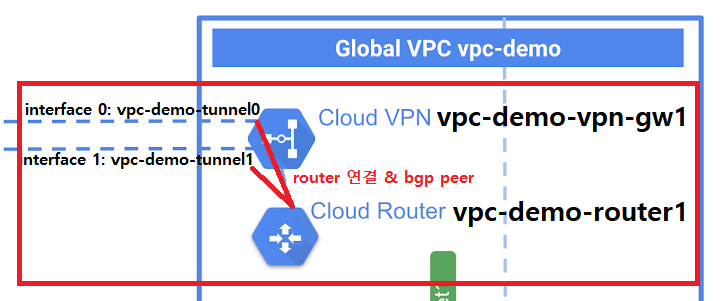
# interface0 에 대한 tunnel0 생성
gcloud compute routers add-interface [인터페이스를 추가할 해당 라우터명] \
--interface-name [인터페이스명] \
--ip-address [연결할 ip] \
--mask-length 30 \
--vpn-tunnel [vpn터널명] \
--region [지역명]
gcloud compute routers add-interface vpc-demo-router1 \
--interface-name if-tunnel0-to-on-prem \
--ip-address 169.254.0.1 \
--mask-length 30 \
--vpn-tunnel vpc-demo-tunnel0 \
--region us-central1
# tunnel0 bgp peer
gcloud compute routers add-bgp-peer [bgp-peer 할 라우터명] \
--peer-name [피어링명] \
--interface [인터페이스명] \
--peer-ip-address [피어할 반대편 ip] \
--peer-asn [피어할 반대편 asn번호] \
--region [지역명]
gcloud compute routers add-bgp-peer vpc-demo-router1 \
--peer-name bgp-on-prem-tunnel0 \
--interface if-tunnel0-to-on-prem \
--peer-ip-address 169.254.0.2 \
--peer-asn 65002 \
--region us-central1
# interface1 에 대한 tunnel1 생성
gcloud compute routers add-interface [인터페이스를 추가할 해당 라우터명] \
--interface-name [인터페이스명] \
--ip-address [연결할 ip] \
--mask-length 30 \
--vpn-tunnel [vpn터널명] \
--region [지역명]
gcloud compute routers add-interface vpc-demo-router1 \
--interface-name if-tunnel1-to-on-prem \
--ip-address 169.254.1.1 \
--mask-length 30 \
--vpn-tunnel vpc-demo-tunnel1 \
--region us-central1
# tunnel1 bgp peer
gcloud compute routers add-bgp-peer [bgp-peer 할 라우터명] \
--peer-name [피어링명] \
--interface [인터페이스명] \
--peer-ip-address [피어할 반대편 ip] \
--peer-asn [피어할 반대편 asn번호] \
--region [지역명]
gcloud compute routers add-bgp-peer vpc-demo-router1 \
--peer-name bgp-on-prem-tunnel1 \
--interface if-tunnel1-to-on-prem \
--peer-ip-address 169.254.1.2 \
--peer-asn 65002 \
--region us-central1
[on-prem tunnel 생성]

# interface0 에 대한 tunnel0 생성
gcloud compute routers add-interface [인터페이스를 추가할 해당 라우터명] \
--interface-name [인터페이스명] \
--ip-address [연결할 ip] \
--mask-length 30 \
--vpn-tunnel [vpn터널명] \
--region [지역명]
gcloud compute routers add-interface on-prem-router1 \
--interface-name if-tunnel0-to-vpc-demo \
--ip-address 169.254.0.2 \
--mask-length 30 \
--vpn-tunnel on-prem-tunnel0 \
--region us-central1
# tunnel0 bgp peer
gcloud compute routers add-bgp-peer [bgp-peer 할 라우터명] \
--peer-name [피어링명] \
--interface [인터페이스명] \
--peer-ip-address [피어할 반대편 ip] \
--peer-asn [피어할 반대편 asn번호] \
--region [지역명]
gcloud compute routers add-bgp-peer on-prem-router1 \
--peer-name bgp-vpc-demo-tunnel0 \
--interface if-tunnel0-to-vpc-demo \
--peer-ip-address 169.254.0.1 \
--peer-asn 65001 \
--region us-central1
# interface1 에 대한 tunnel1 생성
gcloud compute routers add-interface [인터페이스를 추가할 해당 라우터명] \
--interface-name [인터페이스명] \
--ip-address [연결할 ip] \
--mask-length 30 \
--vpn-tunnel [vpn터널명] \
--region [지역명]
gcloud compute routers add-interface on-prem-router1 \
--interface-name if-tunnel1-to-vpc-demo \
--ip-address 169.254.1.2 \
--mask-length 30 \
--vpn-tunnel on-prem-tunnel1 \
--region us-central1
# tunnel1 bgp peer
gcloud compute routers add-bgp-peer [bgp-peer 할 라우터명] \
--peer-name [피어링명] \
--interface [인터페이스명] \
--peer-ip-address [피어할 반대편 ip] \
--peer-asn [피어할 반대편 asn번호] \
--region [지역명]
gcloud compute routers add-bgp-peer on-prem-router1 \
--peer-name bgp-vpc-demo-tunnel1 \
--interface if-tunnel1-to-vpc-demo \
--peer-ip-address 169.254.1.1 \
--peer-asn 65001 \
--region us-central1작업6. 라우터 구성 확인하기
# 라우터 구성 세부정보 확인
gcloud compute routers describe vpc-demo-router1 --region us-central1
gcloud compute routers describe on-prem-router1 --region us-central1
[원격 vpc의 트래픽을 허용하도록 방화벽 규칙 구성]
# on-prem 네트워크에서 vpc-demo 트래픽 허용
gcloud compute firewall-rules create vpc-demo-allow-subnets-from-on-prem \
--network vpc-demo \
--allow tcp,udp,icmp \
--source-ranges 192.168.1.0/24
# vpc-demo 네트워크에서 on-prem 트래픽 허용
gcloud compute firewall-rules create on-prem-allow-subnets-from-vpc-demo \
--network on-prem \
--allow tcp,udp,icmp \
--source-ranges 10.1.1.0/24,10.2.1.0/24작업7. HA VPN 터널 구성확인 및 테스트
# 터널 리스트 확인
gcloud beta compute vpn-tunnels list
[터널 작동 테스트]
* Tunnel is up and running. 이 표시되어야 한다.
# vpc-demo-tunnel0
gcloud beta compute vpn-tunnels describe vpc-demo-tunnel0 --region us-central1
# vpc-demo-tunnel1
gcloud beta compute vpn-tunnels describe vpc-demo-tunnel1 --region us-central1
# on-prem-tunnel0
gcloud beta compute vpn-tunnels describe on-prem-tunnel0 --region us-central1
# on-prem-tunnel1
gcloud beta compute vpn-tunnels describe on-prem-tunnel1 --region us-central1
[vpn을 통한 비공개 연결 확인]
# on-prem 인스턴스 ssh 접속
gcloud compute ssh on-prem-instance1 --zone us-central1-a
y
enter*2
# ping test
ping -c 3 10.1.1.2
[vpn을 사용한 글로벌 라우팅(new tab)]
# 라우팅 설정
gcloud compute networks update vpc-demo --bgp-routing-mode GLOBAL
# 변경사항 확인
gcloud compute networks describe vpc-demo
# 다시 ssh탭에서 ping
ping -c 3 10.2.1.2
[터널 고가용성(HA) 확인]
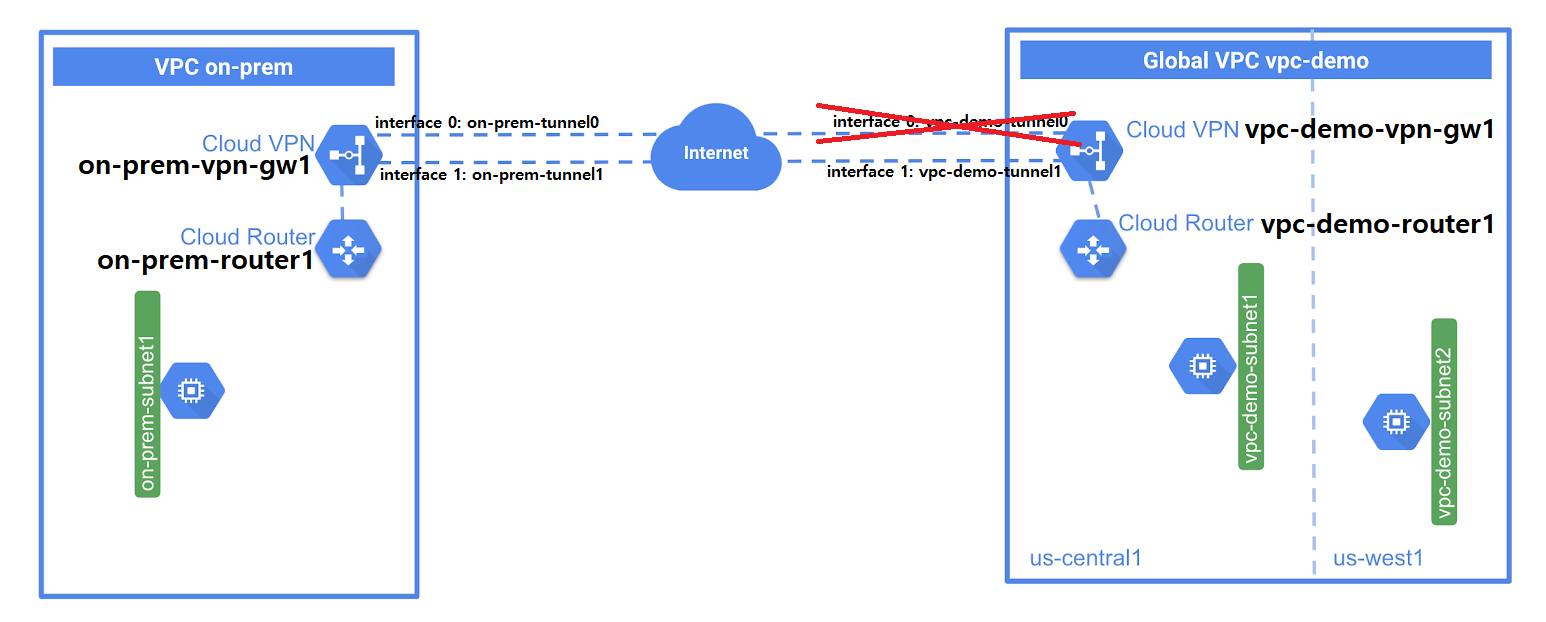
# vpc-demo tunnel0 네트워크 다운시키기
gcloud compute vpn-tunnels delete vpc-demo-tunnel0 --region us-central1
y
# 터널 다운되었는지 확인
gcloud compute vpn-tunnels describe on-prem-tunnel0 --region us-central1
# ssh instance에서 ping 확인
** ping test가 성공해야한다.
ping 10.1.1.2작업8. 실습환경 삭제
# vpn 터널삭제
gcloud compute vpn-tunnels delete on-prem-tunnel0 --region us-central1
gcloud compute vpn-tunnels delete vpc-demo-tunnel1 --region us-central1
gcloud compute vpn-tunnels delete on-prem-tunnel1 --region us-central1
# BGP 피어링 제거
gcloud compute routers remove-bgp-peer vpc-demo-router1 --peer-name bgp-on-prem-tunnel0 --region us-central1
gcloud compute routers remove-bgp-peer vpc-demo-router1 --peer-name bgp-on-prem-tunnel1 --region us-central1
gcloud compute routers remove-bgp-peer on-prem-router1 --peer-name bgp-vpc-demo-tunnel0 --region us-central1
gcloud compute routers remove-bgp-peer on-prem-router1 --peer-name bgp-vpc-demo-tunnel1 --region us-central1
# 클라우드 라우터 삭제
gcloud compute routers delete on-prem-router1 --region us-central1
gcloud compute routers delete vpc-demo-router1 --region us-central1
# vpc 게이트웨이 삭제
gcloud beta compute vpn-gateways delete vpc-demo-vpn-gw1 --region us-central1
gcloud beta compute vpn-gateways delete on-prem-vpn-gw1 --region us-central1
# 인스턴스 삭제
gcloud compute instances delete vpc-demo-instance1 --zone us-central1-b
gcloud compute instances delete vpc-demo-instance2 --zone us-east1-b
gcloud compute instances delete on-prem-instance1 --zone us-central1-a
# 방화벽 규칙 삭제
gcloud beta compute firewall-rules delete vpc-demo-allow-internal
gcloud beta compute firewall-rules delete on-prem-allow-subnets-from-vpc-demo
gcloud beta compute firewall-rules delete on-prem-allow-ssh-icmp
gcloud beta compute firewall-rules delete on-prem-allow-internal
gcloud beta compute firewall-rules delete vpc-demo-allow-subnets-from-on-prem
gcloud beta compute firewall-rules delete vpc-demo-allow-ssh-icmp
# 서브넷 삭제
gcloud beta compute networks subnets delete vpc-demo-subnet1 --region us-central1
gcloud beta compute networks subnets delete vpc-demo-subnet2 --region us-east1
gcloud beta compute networks subnets delete on-prem-subnet1 --region us-central1
# vpc 삭제
gcloud compute networks delete vpc-demo
gcloud compute networks delete on-prem
'GCP > Qwiklabs' 카테고리의 다른 글
| 220901_Automating Infrastructure on Google Cloud with Terraform: Challenge Lab (1) | 2022.09.02 |
|---|---|
| 220901_Interact with Terraform Modules (0) | 2022.09.01 |
| 220831_Infrastructure as Code with Terraform (0) | 2022.08.31 |
| 220830_Terraform Fundamentals (0) | 2022.08.31 |
| 220704_Kubernetes Engine: Qwik Start (0) | 2022.07.04 |



