JINIers
create vpc.yaml 본문
# create vpc
vpc, igw, routing table, security group, 1 ec2(install nginx)
# create vpc.yaml
AWSTemplateFormatVersion: "2010-09-09"
Description: "Create 1 VPC, 4 subnet(public, private), 1 igw, 1 routingtable, 1 Security group, 1 ec2 "
Parameters:
AMI:
Type: AWS::SSM::Parameter::Value<AWS::EC2::Image::Id>
Description: 'The ID of the AMI.'
Default: /aws/service/ami-amazon-linux-latest/al2023-ami-kernel-6.1-x86_64
Resources:
# Create VPC
vpcA:
Type: AWS::EC2::VPC
Properties:
CidrBlock: 10.1.0.0/16
EnableDnsSupport: 'true'
EnableDnsHostnames: 'true'
InstanceTenancy: default
Tags:
- Key: Name
Value: "vpcA"
# Create Subnet
PublicSubnetA:
Type: AWS::EC2::Subnet
Properties:
VpcId:
Ref: vpcA
CidrBlock: 10.1.10.0/24
AvailabilityZone: "ap-northeast-2a"
MapPublicIpOnLaunch: "true"
Tags:
- Key: Name
Value: "Public Subnet AZ1"
PrivateSubnetA:
Type: AWS::EC2::Subnet
Properties:
VpcId:
Ref: vpcA
CidrBlock: 10.1.15.0/24
AvailabilityZone: "ap-northeast-2a"
Tags:
- Key: Name
Value: "Private Subnet AZ1"
PublicSubnetB:
Type: AWS::EC2::Subnet
Properties:
VpcId:
Ref: vpcA
CidrBlock: 10.1.40.0/24
AvailabilityZone: "ap-northeast-2b"
MapPublicIpOnLaunch: "true"
Tags:
- Key: Name
Value: "Public Subnet AZ2"
PrivateSubnetB:
Type: AWS::EC2::Subnet
Properties:
VpcId:
Ref: vpcA
CidrBlock: 10.1.45.0/24
AvailabilityZone: "ap-northeast-2b"
Tags:
- Key: Name
Value: "Private Subnet AZ2"
# Create Public Route Table
PublicRouteTable:
Type: AWS::EC2::RouteTable
Properties:
VpcId:
Ref: vpcA
Tags:
- Key: Name
Value: "PublicRouteTable"
PublicSubnetARouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
DependsOn:
- "PublicRouteTable"
- "PublicSubnetA"
Properties:
RouteTableId:
Ref: PublicRouteTable
SubnetId:
Ref: PublicSubnetA
PublicSubnetCRouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
DependsOn:
- "PublicRouteTable"
- "PublicSubnetB"
Properties:
RouteTableId:
Ref: PublicRouteTable
SubnetId:
Ref: PublicSubnetB
# Create Internet GateWay
igw:
Type: AWS::EC2::InternetGateway
Properties:
Tags:
- Key: Name
Value: "igw"
vpcAInternetGatewayAttachment:
Type: AWS::EC2::VPCGatewayAttachment
DependsOn:
- vpcA
- igw
Properties:
VpcId: !Ref vpcA
InternetGatewayId: !Ref igw
vpcAInternetRoute:
Type: AWS::EC2::Route
DependsOn: igw
Properties:
RouteTableId:
Ref: PublicRouteTable
DestinationCidrBlock: 0.0.0.0/0
GatewayId:
Ref: igw
# Create Security Group
WebSG:
Type: AWS::EC2::SecurityGroup
DependsOn: vpcA
Properties:
GroupDescription: Web APP Security Group
GroupName: "Web-SG"
VpcId: !Ref vpcA
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: 80
ToPort: 80
CidrIp: 0.0.0.0/0
- IpProtocol: icmp
FromPort: -1
ToPort: -1
CidrIp: 0.0.0.0/0
- IpProtocol: tcp
FromPort: 22
ToPort: 22
CidrIp: 0.0.0.0/0
- IpProtocol: -1
CidrIp: 0.0.0.0/0
Tags:
- Key: Name
Value: "web-sg"
# instance
webec2:
Type: AWS::EC2::Instance
DependsOn:
- PublicSubnetA
- WebSG
Properties:
ImageId: !Ref AMI
KeyName: "test"
InstanceType: t2.micro
NetworkInterfaces:
- AssociatePublicIpAddress: true
SubnetId: !Ref PublicSubnetA
DeviceIndex: "0"
GroupSet:
- !Ref WebSG
Tags:
- Key: Name
Value: "web-ec2"
UserData:
Fn::Base64: !Sub |
#!/bin/bash -xe
sudo su
yum install nginx -y
systemctl enable nginx
systemctl start nginx
실행결과
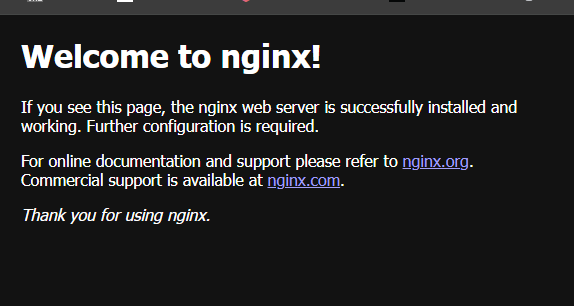
※ security group ingress 참고
인바운드 규칙 내 모든트래픽으로 통신하는 것으로 설정하고 싶다면 ▼
- IpProtocol: -1
CidrIp: 0.0.0.0/0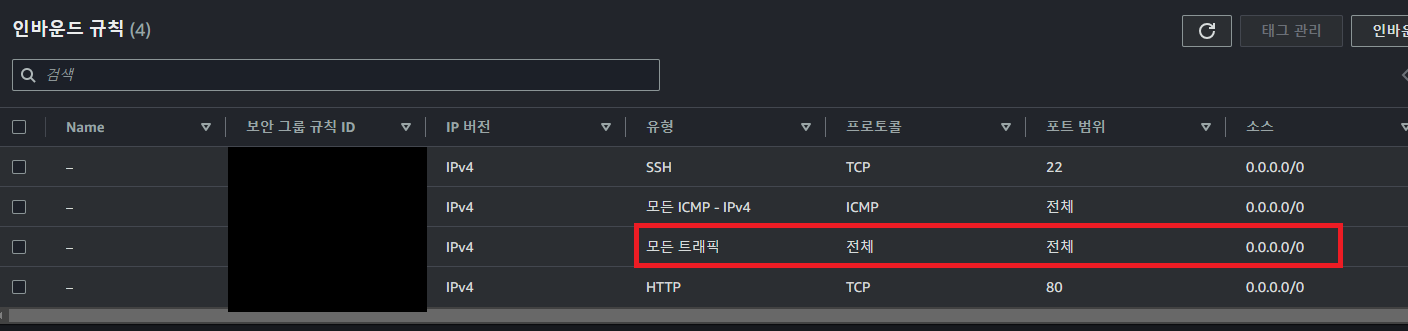
create-vpc.yaml
0.00MB
'AWS > 이것저것' 카테고리의 다른 글
| cloudformaiton 이용 네트워크 구성하기(autoscaling 생성) (0) | 2024.03.29 |
|---|---|
| cloudformaiton 이용 네트워크 구성하기(LB 생성) (0) | 2024.03.29 |
| cloudformaiton 이용 네트워크 구성하기(vpc 생성) (0) | 2024.03.29 |
| S3 이용 서버리스 구축 (0) | 2024.03.19 |
| 동적 사이트 구축.yaml (0) | 2024.03.14 |



